RemoteIoT VPC SSH AWS - Connecting Your Devices
Getting your distant devices to chat safely with your main setup can feel a bit like a puzzle, especially when you think about all the pieces involved. People are really looking for ways to manage things far off, like tiny sensors or bigger machines, without having to be right there. This kind of setup, where things talk to each other over long distances, is becoming more and more common, you know, in lots of different places. It's about making sure your devices can send their messages and get their instructions back, all while keeping everything private and sound.
When you are dealing with devices that are not close by, perhaps in a factory or out in the field, making sure they can communicate without issues is a big deal. You want to be sure that only the right people or systems can reach them, and that any information going back and forth stays private. This is where thinking about how these connections are made, and what tools help keep them secure, becomes pretty important. It's a way to keep things running smoothly, you know, even when you're not physically present with the equipment.
We are going to look at some key ideas that help make this possible. We will talk about private network spaces, secure ways to log in, and how a big cloud service can bring it all together. It's about building a reliable pathway for your remote things, so they can do their job, and you can keep an eye on them. This helps make sure your remote operations are both effective and, in some respects, very secure.
Table of Contents
- What is RemoteIoT and Why Do We Care?
- The Idea of Remote IoT Devices
- What is a VPC and How Does It Help with AWS?
- Setting Up Your Own Private VPC Space
- How Does SSH Fit Into This Remote Picture?
- Making Sure Your SSH Access is Secure
- Bringing It All Together with AWS
- Connecting Your RemoteIoT Devices Through AWS
What is RemoteIoT and Why Do We Care?
Remote IoT, or the Internet of Things, involves physical items that have sensors, software, and other technologies built into them. These items connect and exchange data with other devices and systems over the internet. The "remote" part just means these things are not right next to you. They could be in a far-off farm, a city street, or even deep inside a factory. So, it's about getting information from places you cannot easily visit, you know, on a regular basis.
People care about this because it helps them make better choices and automate tasks. Think about smart streetlights that tell you when they need fixing, or sensors in a field that report on soil moisture. These remote items gather information that helps us understand things better and react more quickly. It's a way to extend our reach, you might say, and get real-time updates from distant spots. This can lead to big savings and more effective operations, too it's almost a way of being everywhere at once.
The core idea is to collect data from these far-flung gadgets and then use that data for something useful. Maybe it is to control something, or perhaps to simply monitor conditions. Without a good way to connect to them, these remote items would just be isolated pieces of hardware. So, having a solid communication channel is, in some respects, very vital for their purpose. That's why we really pay attention to how these connections are made and kept safe.
- Aditi Mistry Viral
- Subhashree Sahu New Leaks
- Why Did Russell Crowe Gain Weight
- Grace Sward Gdp
- Aditimistry Leaks
The Idea of Remote IoT Devices
When we talk about remote IoT devices, we are thinking about all sorts of things. This could mean a small temperature sensor in a refrigerated truck that sends updates on its cargo's condition. Or, it might be a big industrial machine in a faraway plant that sends performance data back to headquarters. The key thing is that these devices are not typically connected directly to your office network; they need a special way to get their messages across. That, is that, a big part of the challenge.
These devices often have limited processing power and battery life, too it's almost a given. They are built to do one or two specific jobs very well, like measuring something or turning a switch. So, the way they connect needs to be simple, efficient, and not use up too much energy. Getting them to talk to a central system securely, without a lot of fuss, is what people are aiming for. It's about making sure these tiny brains can whisper their secrets safely across long distances, you know, without much trouble.
The information they send back helps businesses make smarter choices. For example, knowing the exact temperature inside a cold storage unit helps prevent spoilage. Or, getting alerts from a pump in a remote oil field can prevent a costly breakdown. This kind of remote monitoring, you know, helps keep things running smoothly and prevents big problems before they even start. It’s a pretty clever way to manage assets that are far from your direct sight.
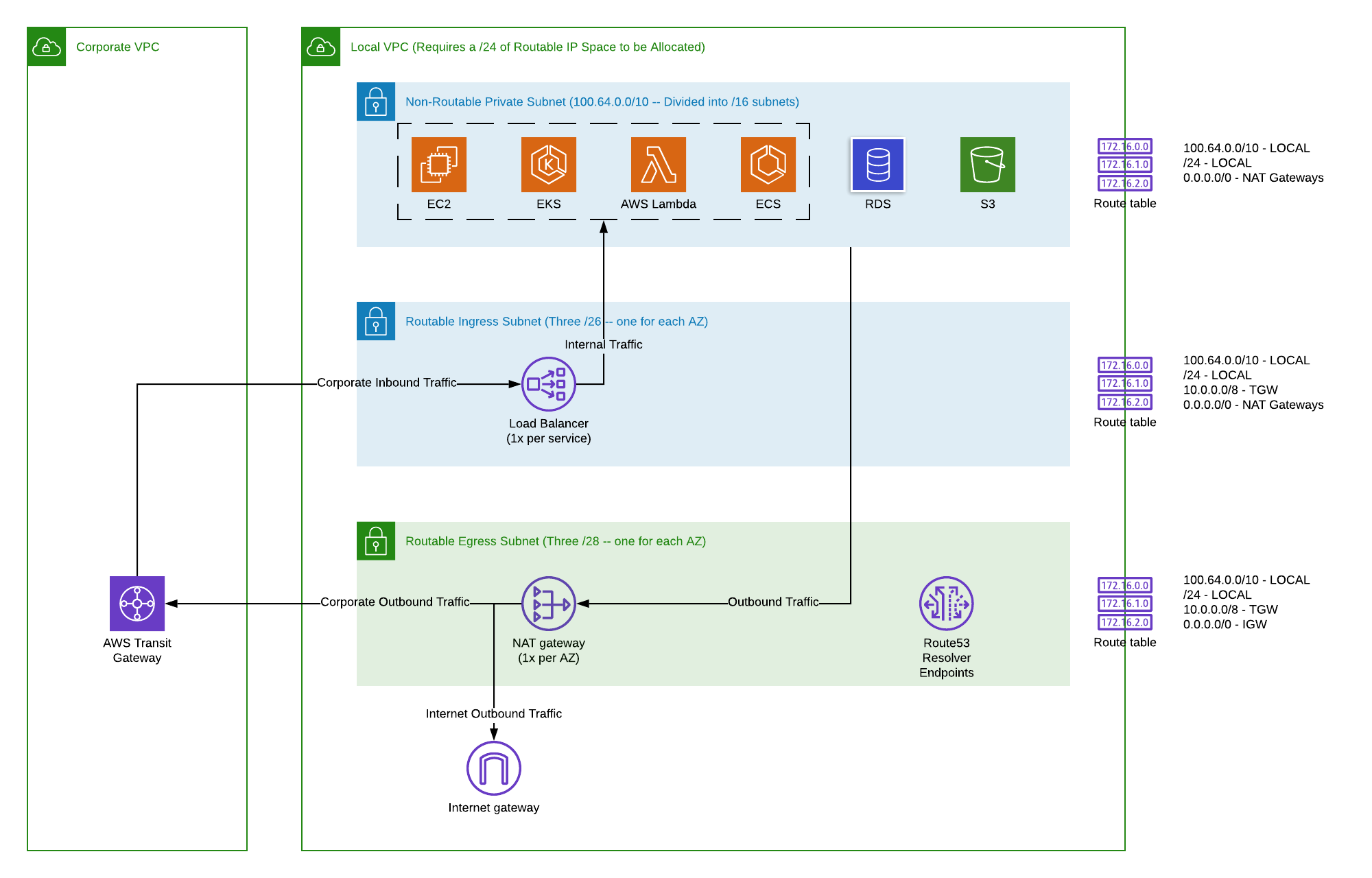
What is a VPC and How Does It Help with AWS?
A VPC, which stands for Virtual Private Cloud, is like having your very own private section of a public cloud. Imagine a big apartment building, which is the public cloud. A VPC is like your specific apartment within that building. You have your own walls, your own doors, and you decide who gets to come in. Other people in the building have their own apartments, but they cannot just walk into yours. This separation helps keep your things separate and, in some respects, very secure from everyone else's. So, it's a way to have your own space, even though you are sharing the building.
When you use a service like AWS, a VPC gives you control over your network environment. You get to pick your own IP address ranges, set up subnets (smaller sections within your private area), and configure route tables and network gateways. This means you can decide exactly how your resources inside the VPC talk to each other and how they talk to the internet. It's a bit like being an architect for your own digital space, you know, giving you a lot of say in how things are laid out.
This private space is really important for security. Because it is isolated, it is much harder for unauthorized people to get to your data or your remote IoT devices. You can set up strict rules about what traffic can come in and what can go out. This level of control helps protect your sensitive information and your connected equipment. It's a pretty fundamental building block for keeping your cloud operations safe and, actually, quite orderly.
Setting Up Your Own Private VPC Space
Setting up your own private VPC space involves a few steps, but it gives you a lot of say in how your network behaves. First, you pick a range of IP addresses that only your VPC will use. This is like deciding on the street numbers for your private neighborhood. Then, you can divide that range into smaller sections called subnets. You might have one subnet for your web servers and another for your databases, for example. This helps keep different types of resources separated, you know, for better organization.
You also get to decide how traffic flows in and out of your VPC. You can set up internet gateways if you want your resources to talk to the public internet. Or, you might use VPN connections to link your VPC back to your own office network. This flexibility means you can build a network setup that fits your exact needs, whether it is for a small project or a big enterprise system. It's really about custom tailoring your network environment, so it works just the way you want it, more or less.
The security features within a VPC are pretty good, too it's almost like having a bouncer at every door. You can use security groups, which are like firewalls for individual resources, and network access control lists (NACLs), which control traffic for entire subnets. These tools let you specify exactly what kind of network traffic is allowed. This layered approach helps protect your remote IoT devices and other data from unwanted visitors, you know, keeping everything locked down tight.
How Does SSH Fit Into This Remote Picture?
SSH, or Secure Shell, is a way to get into a computer or server that is far away, but in a very safe manner. Imagine you need to fix something on a computer that is hundreds of miles away. You cannot just walk up to it. SSH lets you connect to it over the internet, and it makes sure that no one can listen in on your conversation or pretend to be you. It's like having a super-secret, encrypted phone line directly to that remote machine, you know, so your commands are private.
For remote IoT setups, SSH is often used to manage the devices themselves or the servers that collect data from them. You might need to log into an IoT gateway to update its software, or check a log file on a server that is processing sensor readings. SSH provides that secure pathway. Without it, you would have to physically go to each device, which is, in a way, just not practical for things that are far away or in large numbers. It really makes remote administration possible, you know, with peace of mind.
The "secure" part of Secure Shell is really important. It uses strong encryption to scramble all the information that passes between your computer and the remote device. This means that even if someone manages to intercept the data, they cannot make sense of it. This protection is pretty essential when you are dealing with sensitive data or critical systems. So, it is a key tool for keeping your remote operations both functional and, in some respects, very private.
Making Sure Your SSH Access is Secure
Making sure your SSH access is secure involves a few good habits. First, you should always use strong passwords, or even better, SSH keys. SSH keys are like super-long, complex passwords that are nearly impossible for someone to guess. You have one part on your computer and another part on the remote device, and they have to match perfectly for you to get in. This is a much safer way to log in than just typing a password, you know, every time.
Another good practice is to limit who can access your remote devices using SSH. Not everyone needs to be able to log in. You can set up rules that only allow connections from specific IP addresses, like your office network. This helps reduce the chances of someone unwanted trying to get in. It's like putting a guest list on the door, so only invited people can even try to enter, more or less.
Keeping your software updated is also a big part of SSH security. Developers often release updates that fix security holes. If you do not update, you might be leaving a door open for someone to exploit. So, regularly checking for and applying updates to your SSH client and server software is, in a way, very important. It's a continuous effort, you know, to stay ahead of potential problems and keep your connections safe.
Bringing It All Together with AWS
AWS, or Amazon Web Services, is a big collection of cloud services that lets you build and run all sorts of things online. Think of it as a massive toolbox with every kind of tool you could possibly need for building digital stuff. For remote IoT, VPCs, and SSH, AWS provides the platform where all these pieces can live and work together. It gives you the computing power, the network infrastructure, and the security features you need to make your remote operations happen. This means you do not have to buy and maintain your own physical servers, you know, saving a lot of effort.
With AWS, you can create your VPC, launch servers within it, and then connect your remote IoT devices to those servers. AWS offers services that are specifically for IoT, which help manage all those connected devices, collect their data, and even send commands back to them. It is like having a central command center for all your distant gadgets. This integrated approach makes it easier to scale up your operations, too it's almost like magic, as you add more devices or need more processing power.
The benefit of using a service like AWS is that it handles a lot of the underlying work for you. You do not have to worry about the physical hardware or the basic network setup. You can focus on what your remote IoT devices are supposed to do and how they provide value. AWS also has many security features built in, which helps protect your data and connections. So, it provides a pretty reliable and scalable foundation for your entire remote setup, you know, making things much simpler.
Connecting Your RemoteIoT Devices Through AWS
Connecting your remote IoT devices through AWS involves setting up a pathway from your devices to your VPC. Often, these devices will send their data to an AWS IoT Core service first. This service is designed to handle a huge number of devices and securely bring their data into the AWS cloud. From there, the data can be routed to servers or databases within your private VPC for processing or storage. It is like a special receiving dock just for your device messages, you know, making sure nothing gets lost.
Once the data is inside your VPC, you can use other AWS services to make sense of it. You might have a small server that analyzes the temperature readings from your sensors, or a database that stores all the historical data. SSH would then be used to securely log into these servers within your VPC to manage them, check on things, or make changes. This way, you have full control over your data processing environment, even though your devices are far away. It's a pretty neat way to keep everything connected and manageable, more or less.
The whole setup provides a robust and flexible way to manage your remote operations. You have the security of a private network space (VPC), the secure access provided by SSH, and the vast resources of AWS to tie it all together. This means you can confidently deploy devices in distant locations, knowing that their communication is protected and that you can manage them effectively. It's about building a reliable bridge between your physical devices and your digital control center, you know, making the distance feel a lot smaller.
This discussion has covered the basics of connecting distant devices using a private cloud space, secure login methods, and a big cloud service. We looked at what remote IoT means for getting data from faraway items, how a VPC gives you your own secure network spot, and how SSH helps you securely reach those distant computers. We also touched on how a service like AWS helps bring all these pieces together, making it easier to manage your remote operations and keep everything safe.
AWS VPC Subnets, Routing Tables And Internet Access Using, 56% OFF

Creating a Virtual Private Cloud (VPC) in AWS: A Step-by-Step guide

AWS — Difference between VPC Peering and Transit Gateway | by Ashish