Securely Connect RemoteIoT VPC AWS Not Working- What To Do
It can feel quite frustrating when your remote IoT devices just won't link up with your AWS Virtual Private Cloud. You try to set things up for a secure connection, expecting everything to click into place, and then, well, it doesn't. This kind of hiccup, where you're trying to securely connect remote IoT VPC AWS but it's not working, is something many folks run into. It often leaves you scratching your head, wondering what part of the puzzle is out of place.
This situation, where your setup for a secure connection between remote IoT and your AWS VPC seems to hit a wall, is a common one. It might make you question if you missed a step or if there's some hidden setting that needs a tweak. The promise of smooth linking for your devices to the cloud is a big one, so it's a bit of a letdown when the actual experience brings unexpected roadblocks. You just want your things to talk to each other safely, and when they don't, it's a bother, you know?
So, this article is here to help you sort through those moments of confusion. We will go through the usual suspects behind why your setup for securely connecting remote IoT VPC AWS might be having trouble. We'll break down each bit, from the core idea of a virtual network to the smaller points that often get overlooked. It's about getting your remote devices to talk to AWS in a safe way, which is super important for keeping your information good and your systems running well, as a matter of fact.
- Aroomi Kim Erome
- Cast Of Beverly Hills Cop Where Are They Now
- Aditi Mostry Nude
- Duckduckgo Vs Ecosia
- Best Iot Ssh P2p Free
Table of Contents
- Why Can't I Securely Connect Remote IoT VPC AWS?
- Checking Your Network Setup for Securely Connecting Remote IoT
- Are Your Security Rules Blocking a Secure Connection to Remote IoT VPC AWS?
- What About Device Settings for Securely Connecting Remote IoT?
- Credentials and Policies for Securely Connecting Remote IoT VPC AWS
- Troubleshooting Steps When Securely Connecting Remote IoT VPC AWS is Not Working
- Common Overlooked Spots When Securely Connecting Remote IoT
- Looking at Logs When Securely Connect Remote IoT VPC AWS is Not Working
Why Can't I Securely Connect Remote IoT VPC AWS?
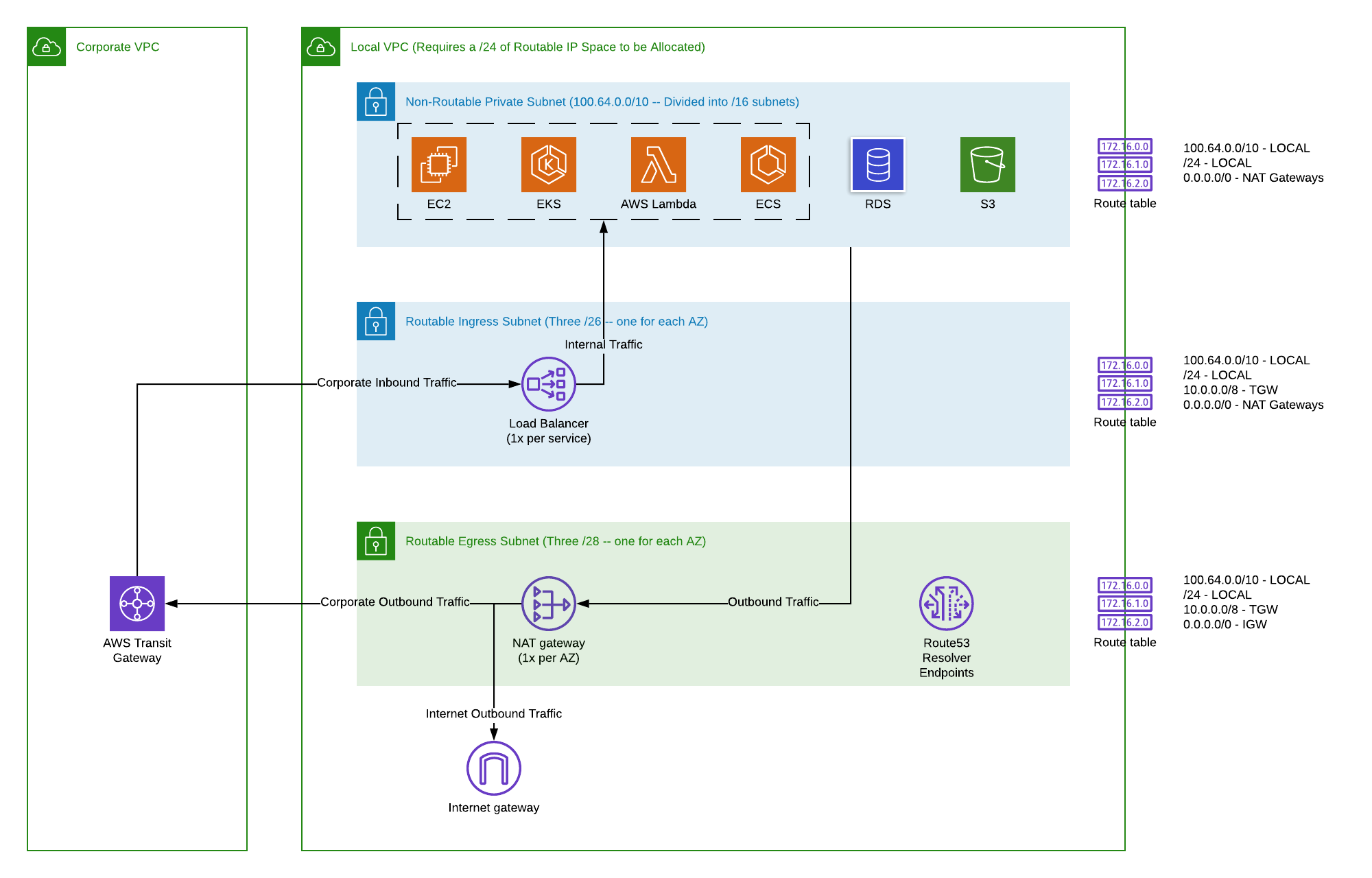
Many things can make it hard to securely connect your remote IoT devices to an AWS Virtual Private Cloud. It's a bit like trying to send a letter, but the address is wrong, or the post office is closed. One main reason is often how the network itself is set up. A Virtual Private Cloud, or VPC, is like your own private section of the internet inside AWS. It's where your services live, and your IoT devices need a clear, safe path to get there. Sometimes, the way this path is drawn out can have a few bumps, so it's almost a good idea to check that first.
Another common spot for trouble is with the safety rules you put in place. You want your connection to be safe, of course, but sometimes these very rules can be too strict, accidentally keeping your own devices out. This includes things like security groups and network access control lists, which are like bouncers at a club, deciding who gets in and who doesn't. If they're not told to let your IoT devices through, then they won't, and that's a problem for securely connecting remote IoT VPC AWS, you know?
Then there's the device itself. Your little Raspberry Pi or other IoT gadget needs to be set up just right on its end. It's not just about the cloud side; the device needs to know where to send its messages and how to make sure they are private. If the device's own settings are off, or if it's using an old piece of software, it might not be able to talk to AWS properly. This is a big part of why securely connecting remote IoT VPC AWS might not work as you hope, as a matter of fact.
- Subhasree Sahu Viral
- Jayshree Gaikwad
- Subhashree Sahu Video Leaked
- Thea Fabregas
- Niki Minhaj Is Onlyfans And Singer
Checking Your Network Setup for Securely Connecting Remote IoT
When you're trying to get your remote IoT devices to talk to your AWS setup, the very first place to look is your network. Think of your VPC as a house with many rooms, and your IoT device is trying to visit. You need to make sure the house has an open door, and that the device knows which door to use. This means checking your VPC settings, like your subnets and routing tables. Are your subnets set up to let traffic flow in the way you expect? Are your routing tables telling the data where to go once it enters your VPC? These are basic but very important parts of securely connecting remote IoT.
Sometimes, the issue is simply that the network path isn't complete. Maybe there's no internet gateway attached to your VPC, or if you're using a private connection, maybe the VPN or Direct Connect link isn't quite right. Each piece of the network puzzle needs to fit together for a smooth flow of information. It's a bit like building a bridge; if one piece is missing, the bridge doesn't work. So, take a good look at all the network bits that help you securely connect remote IoT VPC AWS, you know?
Also, consider DNS. Your devices need to be able to find the AWS services they want to talk to, and they do this by looking up names like "iot.amazonaws.com". If your DNS settings within your VPC, or on your device, aren't letting these lookups happen, then your device won't know where to send its data. It's a small detail, but a very common reason for things not working. Making sure DNS is good is a pretty important step for securely connecting remote IoT, to be honest.
Are Your Security Rules Blocking a Secure Connection to Remote IoT VPC AWS?
Security rules are meant to keep bad stuff out, but sometimes they can be a bit too good at their job, accidentally keeping good stuff out too. When you're trying to securely connect remote IoT VPC AWS, you have to look closely at your security groups and network access control lists (NACLs). Security groups act like firewalls for your instances, while NACLs work at the subnet level. Both need to have rules that allow your IoT devices to send and receive information on the right ports and using the right protocols. If these rules are too tight, your connection will just stop, you know?
For instance, if your IoT device uses MQTT over port 8883, your security group for the AWS IoT Core endpoint, or any intermediate service, needs to allow incoming traffic on that port. If it doesn't, the connection simply won't happen. It's a common mistake, forgetting to open a specific port that your device needs. This is why checking these rules is a big part of troubleshooting when securely connecting remote IoT VPC AWS is not working, basically.
Remember that NACLs are stateless, meaning they don't remember past connections. If you allow incoming traffic, you also need to explicitly allow outgoing traffic for the replies. Security groups, on the other hand, are stateful, so they remember. This difference can trip people up. So, double-checking both the inbound and outbound rules for both security groups and NACLs is a smart move to make sure your secure connection to remote IoT VPC AWS can happen, anyway.
What About Device Settings for Securely Connecting Remote IoT?
It's easy to focus only on the cloud side of things, but your remote IoT device itself needs to be set up correctly for any connection to work. Think of your Raspberry Pi or other gadget as one half of a conversation. If it's not speaking the right language or isn't listening for a reply, the conversation won't happen. This means checking its network settings, its local firewall, and the software it's running that tries to link to AWS. Is the device's IP address correct? Can it even reach the internet, or its gateway, to begin with? These are pretty fundamental checks for securely connecting remote IoT.
Many IoT devices have their own local firewall settings. Just like the AWS security groups, these can block outgoing or incoming connections if not configured properly. You might have everything perfect on the AWS side, but if your device's own firewall is stopping it from sending data, then nothing will get through. It's a bit like having a locked door on your side of the house when you're trying to invite someone in. So, checking the device's local firewall is a very good step when securely connecting remote IoT VPC AWS is not working, you know?
Also, consider the software on the device that handles the connection. Is it the right version? Is it configured with the correct AWS endpoint? Sometimes, older software versions might not support newer security methods or might have bugs that prevent a stable connection. Making sure your device's software is up-to-date and correctly told where to connect is a key part of getting a secure connection to remote IoT VPC AWS. This is often an overlooked spot, as a matter of fact.
Credentials and Policies for Securely Connecting Remote IoT VPC AWS
Even if your network paths are open and your devices are ready to talk, they need permission to do so. This is where credentials and policies come into play. Your IoT device needs a way to prove who it is to AWS, typically through certificates or other forms of identity. If these credentials are not set up correctly on the device, or if they have expired, AWS will simply refuse the connection. It's like trying to get into a secure building without the right ID card. So, making sure your device has the correct, current credentials is a big part of securely connecting remote IoT VPC AWS.
Beyond just proving its identity, your device also needs to have the right permissions to do what it wants to do within AWS IoT Core. These permissions are defined in policies. For example, a device might need permission to publish messages to a certain topic or to subscribe to another. If the policy attached to your device's identity doesn't grant these specific actions, then even if it connects, it won't be able to do much. This is a common reason why securely connecting remote IoT VPC AWS might seem to work at first, but then nothing happens, you know?
It's also worth checking if the policies are too restrictive or too broad. Sometimes, a policy might accidentally deny an action that your device needs to perform. Or, conversely, if a policy is too open, it might pose a security risk, though that's less about the "not working" part and more about safety. So, carefully reviewing the IoT policies linked to your device's certificates or things is a pretty important step for securely connecting remote IoT VPC AWS, especially when things aren't flowing as they should, to be honest.
Troubleshooting Steps When Securely Connecting Remote IoT VPC AWS is Not Working
When you find that securely connecting remote IoT VPC AWS is not working, having a clear set of steps to check can save you a lot of time and frustration. Start with the basics: can your device even reach the internet? A simple ping to a public website can tell you if its basic network connection is okay. If that works, try pinging the AWS IoT endpoint. This helps figure out if the issue is with your device's local network or with its ability to talk to AWS. It's a pretty straightforward first check, you know?
Next, use tools like `traceroute` or `tracert` from your device. This command shows you the path your data takes to reach its destination. If you see it stopping at a certain point, or if there are unexpected delays, it can point to a firewall, a router, or a network problem somewhere along the way. This kind of network path check is very helpful for understanding where your securely connecting remote IoT VPC AWS data might be getting stuck, as a matter of fact.
Also, check the status of your AWS services. Is AWS IoT Core running as expected? Are there any reported outages in your region? While rare, service issues can happen. Finally, review your AWS console for any error messages related to your IoT devices or VPC. AWS often provides helpful hints right there in the console that can guide you to the problem. These steps, taken one by one, can really help you figure out why securely connecting remote IoT VPC AWS is not working, basically.
Common Overlooked Spots When Securely Connecting Remote IoT
Sometimes, the problems that keep you from securely connecting remote IoT VPC AWS are not big, obvious things, but rather small details that are easy to miss. One common overlooked spot is time synchronization. Your IoT device and AWS need to agree on what time it is for security certificates to work properly. If your device's clock is way off, it might not be able to establish a secure connection, as the certificates will appear invalid. So, making sure your device has accurate time, perhaps through NTP, is a small but very important detail, you know?
Another often-missed point is the specific endpoint your device is trying to connect to. AWS IoT Core has different endpoints for data and for device registration. Your device needs to be pointing to the correct data endpoint for publishing and subscribing. If it's trying to talk to the wrong address, it won't work, even if everything else is perfect. Double-checking that the endpoint URL in your device's configuration is the right one for securely connecting remote IoT VPC AWS is a good idea, as a matter of fact.
Also, consider proxy settings. If your IoT device is behind a corporate network or uses a proxy server to get to the internet, that proxy needs to be configured to allow traffic to AWS IoT endpoints. The proxy itself might also need to trust the AWS certificates. These intermediate network pieces can often be the hidden culprits when securely connecting remote IoT VPC AWS is not working, so it's worth checking if your device goes through one, to be honest.
Looking at Logs When Securely Connect Remote IoT VPC AWS is Not Working
When you are trying to figure out why securely connecting remote IoT VPC AWS is not working, logs are your best friends. Both your IoT device and AWS generate logs that can give you clues about what's going wrong. On your device, check the logs of the application that's trying to connect to AWS. It might show error messages about connection failures, certificate issues, or network timeouts. These messages are often the most direct way to pinpoint a problem on the device side. It's a very good habit to check these first, you know?
On the AWS side, there are several places to look for log information. AWS IoT Core itself provides logging capabilities that can show you if devices are trying to connect, if their certificates are being accepted, or if policies are denying actions. CloudWatch Logs is where much of this information ends up. Looking through these logs can tell you if AWS is even seeing your device's connection attempts and what it's doing with them. This is pretty helpful for securely connecting remote IoT VPC AWS, as a matter of fact.
You should also look at VPC Flow Logs. These logs record information about the IP traffic going to and from network interfaces in your VPC. They can show you if traffic from your IoT device is even reaching your VPC, or if it's being blocked by a security group or NACL. If you see "REJECT" entries for traffic from your device's IP address, that's a strong hint that a security rule is the problem. Using these logs can really help you figure out why securely connecting remote IoT VPC AWS is not working, basically.
- Why Did Callie Torres Leave Greys Anatomy
- Juliana Palvin
- Remoteiot Vpc Price
- Xhmaster
- When Does Callie Leave Grays Anatomy

How To Fix Securely Connect Remote IoT VPC AWS Not Working: A
AWS VPC Subnets, Routing Tables And Internet Access Using, 56% OFF

Securely Connect Remote IoT VPC Raspberry Pi AWS Free: A Comprehensive